evidence encryption 2025-11-14T02:38:09Z
-
 Evidence, Grand CahorsPrepare your travels with the best application Evidence, Grand Cahors.The application Evidence, Grand Cahors offers all the features to travel on your transit network: real-time and theoretical schedules, traffic info, route search, plans.Consult with one click the next passages in real time at the stops closest to you!Easily find the last stops that you have searched for and add your stop to favorites in one click.Why use Evidence, Grand Cahors?Be on time: check the waitin
Evidence, Grand CahorsPrepare your travels with the best application Evidence, Grand Cahors.The application Evidence, Grand Cahors offers all the features to travel on your transit network: real-time and theoretical schedules, traffic info, route search, plans.Consult with one click the next passages in real time at the stops closest to you!Easily find the last stops that you have searched for and add your stop to favorites in one click.Why use Evidence, Grand Cahors?Be on time: check the waitin -
 The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore.
The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore. -
 AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil
AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil -
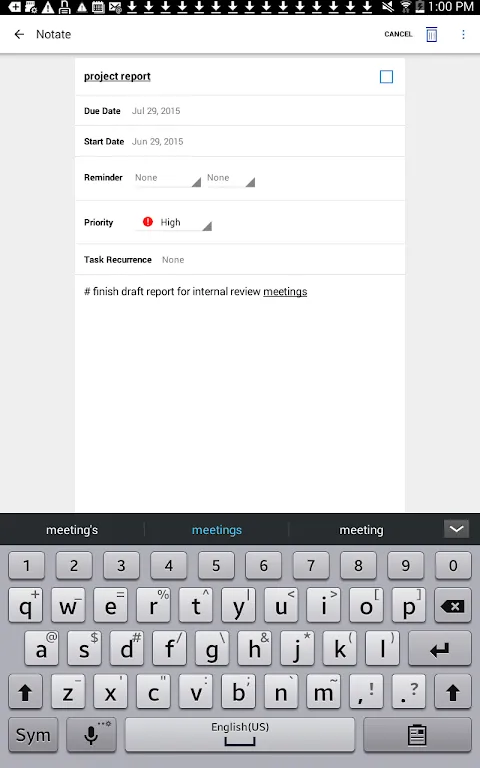 Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor
Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 Indian Evidence Act 1872 (IEA)Refer to Bharatiya Sakshya Adhiniyam, 2023 in Law App for latest Criminal Reforms in India\xe2\x80\x98Indian Evidence Act 1872 (IEA)\xe2\x80\x99 is the Best Indian Evidence Act learning App with latest Amendments. It is a free and offline app providing detail Section-wi
Indian Evidence Act 1872 (IEA)Refer to Bharatiya Sakshya Adhiniyam, 2023 in Law App for latest Criminal Reforms in India\xe2\x80\x98Indian Evidence Act 1872 (IEA)\xe2\x80\x99 is the Best Indian Evidence Act learning App with latest Amendments. It is a free and offline app providing detail Section-wi -
 Police & Criminal Evidence Act\xe2\x80\x98Police & Criminal Evidence Act\xe2\x80\x99 is the Best Police and Criminal Evidence Act 1984 learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of Police and Criminal Evidence Ac
Police & Criminal Evidence Act\xe2\x80\x98Police & Criminal Evidence Act\xe2\x80\x99 is the Best Police and Criminal Evidence Act 1984 learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of Police and Criminal Evidence Ac -
 eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa
eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa -
 Evidenced Based Medicine GuideEvidence-Based Medicine Guidelines (EBMG) is an easy-to-use collection of clinical guidelines for primary and ambulatory care linked to the best available evidence. Continuously updated, EBMG follows the latest developments in clinical medicine and brings evidence into practice.EBMG is designed to provide you with the information you need quickly (seconds, not minutes) and using a single search term. Designed for use at the point of care, the guidelines are delivere
Evidenced Based Medicine GuideEvidence-Based Medicine Guidelines (EBMG) is an easy-to-use collection of clinical guidelines for primary and ambulatory care linked to the best available evidence. Continuously updated, EBMG follows the latest developments in clinical medicine and brings evidence into practice.EBMG is designed to provide you with the information you need quickly (seconds, not minutes) and using a single search term. Designed for use at the point of care, the guidelines are delivere -
 Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res
Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res -
 Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f
Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f -
 Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m
Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m -
 Granny's Silent ResidenceImmerse yourself in cinematic horror that will not let you go until the very end of the mysterious story. Enjoy dynamic first-person cutscenes and take part in an incredible storyline.Dare you to challenge your fears and travel to an old abandoned evil house in a village in the hills and unravel all the disturbing secrets?Do you remember that your granny told you scary tales about a silent, abandoned playhouse where the evil spirit lady Hasshaku-sama (or slendrina for ex
Granny's Silent ResidenceImmerse yourself in cinematic horror that will not let you go until the very end of the mysterious story. Enjoy dynamic first-person cutscenes and take part in an incredible storyline.Dare you to challenge your fears and travel to an old abandoned evil house in a village in the hills and unravel all the disturbing secrets?Do you remember that your granny told you scary tales about a silent, abandoned playhouse where the evil spirit lady Hasshaku-sama (or slendrina for ex -
 The Eminence in Shadow RPGPlay the all-new online fantasy RPG based on the new hit anime, The Eminence in Shadow!\xe2\x97\x86 Experience The Eminence in Shadow's epic story modes!Continue the story with new chapters, beat exciting new challenges and get the latest characters after every new episode
The Eminence in Shadow RPGPlay the all-new online fantasy RPG based on the new hit anime, The Eminence in Shadow!\xe2\x97\x86 Experience The Eminence in Shadow's epic story modes!Continue the story with new chapters, beat exciting new challenges and get the latest characters after every new episode -
 EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me
EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me -
 Rain lashed against the taxi window as we crawled through Piccadilly Circus, taillights bleeding into watery smears. My editor's frantic Slack messages kept pinging - our whistleblower's evidence needed uploading now, before the midnight deadline. When gridlock froze us completely, I spotted the "FreeTubeWiFi" network. Every nerve screamed as I connected, imagining data harvesters circling like digital vultures. That's when the crimson shield icon caught my eye - Touch VPN, installed weeks ago d
Rain lashed against the taxi window as we crawled through Piccadilly Circus, taillights bleeding into watery smears. My editor's frantic Slack messages kept pinging - our whistleblower's evidence needed uploading now, before the midnight deadline. When gridlock froze us completely, I spotted the "FreeTubeWiFi" network. Every nerve screamed as I connected, imagining data harvesters circling like digital vultures. That's when the crimson shield icon caught my eye - Touch VPN, installed weeks ago d -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
 Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv.
Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv. -
 The drizzle blurred my train window into a watercolor smear of grays and greens, that familiar numbness creeping into my bones. Another soul-crushing commute. I fumbled with my phone, thumb hovering over mindless puzzle games – digital pacifiers for the terminally bored. Then I tapped Project VOID's jagged eye icon. Within minutes, I was sprinting through Hammersmith Station, rain soaking my collar, because a pigeon's feather stuck to a wet bench wasn't debris. It was evidence.
The drizzle blurred my train window into a watercolor smear of grays and greens, that familiar numbness creeping into my bones. Another soul-crushing commute. I fumbled with my phone, thumb hovering over mindless puzzle games – digital pacifiers for the terminally bored. Then I tapped Project VOID's jagged eye icon. Within minutes, I was sprinting through Hammersmith Station, rain soaking my collar, because a pigeon's feather stuck to a wet bench wasn't debris. It was evidence. -
 TellaTella . In challenging environments--with limited or no internet connectivity or in the face of repression--Tella makes it easier and safer to document events, whether that\xe2\x80\x99s violence, human rights violations, corruption, or electoral fraud.ENCRYPTION: All of the content and data stored in Tella are encrypted. This means that unless the app is unlocked, all the data within Tella will remain inaccessible.FILE MANAGEMENT: Take photos, videos, or audio recordings directly in Tella,
TellaTella . In challenging environments--with limited or no internet connectivity or in the face of repression--Tella makes it easier and safer to document events, whether that\xe2\x80\x99s violence, human rights violations, corruption, or electoral fraud.ENCRYPTION: All of the content and data stored in Tella are encrypted. This means that unless the app is unlocked, all the data within Tella will remain inaccessible.FILE MANAGEMENT: Take photos, videos, or audio recordings directly in Tella,